Passwordless authentication becomes a reality, really
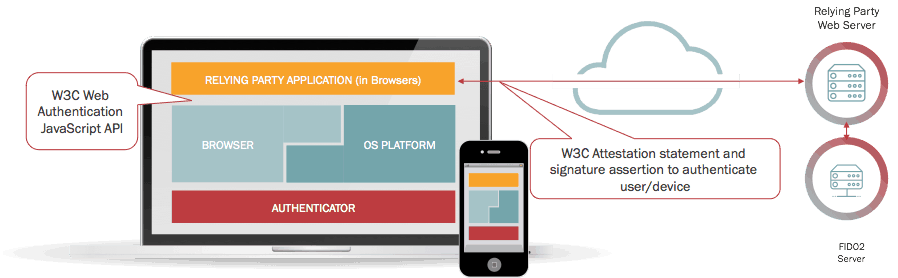
Passwordless authentication has finally come of age. The final piece of the puzzle is what is happening at Apple and their support of the various FIDO2 standards, including adding the Web Authn protocols to Safari running on iOS v14 devices. These protocols are useful, because web application servers can integrate with strong authenticators already built into devices, such as Apple Touch ID/Face ID, Android and Windows Hello. This means that these servers can authenticate the user without directly receiving any private keys or any shared secrets. One of the largest MNOs NTT DOCOMO in Japan already deploys actual passwordless apps.
Before Apple’s implementation, there was ubiquitous support for FIDO across native mobile applications on Android and iOS devices, but not for browser applications. Microsoft, Google and Firefox Mozilla added FIDO support for browsers but, without support in Safari, there was a gap to achieving passwordless. Many organizations were waiting to see if Apple would jump on the bandwagon.
Why is this particular Apple implementation important? There are several reasons. First, biometrics are now used by more people and found in more phones than ever before. Duo reports in a 2019 survey that 77% of smartphones have biometrics configured. Next, before FIDO2 you had to combine device firmware with specific software and an app that was written for this task. Now you have a standards-based approach that will work with any of the major browsers in any context. It also means that finally we can ditch our one-time password apps on our smartphones (such as Authy, Lastpass and Google and Microsoft Authenticators) and your HW OTP Tokens and just use the phones themselves as authentication devices. Finally, this makes FIDO passwordless logins the most secure mechanism of authentication and also the easiest to use. We no longer have to ask users to trade off usability with security: they can have both.
Certainly, there have been other passwordless applications outside of the FIDO effort, as mentioned in this piece in CSOonline. But all of these share common drawbacks: they are vendor-specific, they require special code to integrate with their authentication servers, they make use of existing authentication smartphone apps or they haven’t been tested at the scale that can be used by global enterprises. Speaking of which, FIDO implementations are being used today by millions of users, and they also save time and frustration. Intuit found that their FIDO-enabled mobile app had three major benefits: it cut down on phishing attempts, reduced by 20% the login times for users, and improved by 6% the number of successful logins. They are working on integrating FIDO into their websites’ logins.
Passwords are painful, no doubt. We have too many of them to easily remember, and the number of multi-factor solutions have usability compromises that require a security expert to explain and deploy. It is time to take advantage of FIDO and it is timely that we have the support by Apple of WebAuthn. This could well be a watershed event for mobile ecommerce, making a big incentive for using your smartphone for making online purchases. No more having to download an app for buying from an online storefront when you can just use your browser on iOS, Android, or Windows. You have a simple login and you can get better security than you had before.