How BBVA is using FIDO to protect their customer accounts
Does your bank still think using SMS one-time passcodes are the only additional authentication factors? Mine still does, and I wish I could easily switch to another bank that is more enlightened about their security, such as BBVA. This international bank, which has customers in Spain, the US, Mexico and South America, has been a big supporter of FIDO authentication protocols and uses the Nok Nok S3 Authentication Suite.
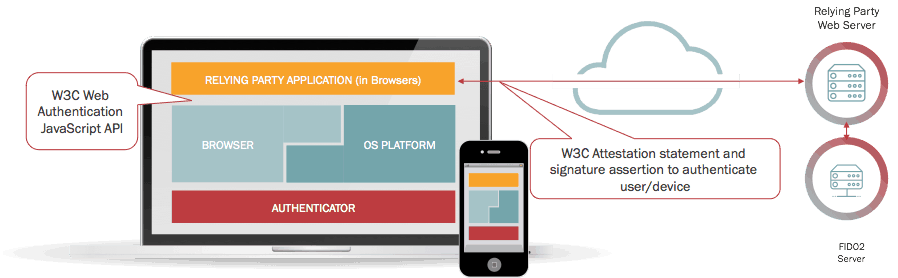
Banking is one of the last bastions of old world thinking when it comes to authentication. A quick scan of a directory of banks offering multifactor authentication (MFA) show that most are still stuck in the past. BBVA is the first Spanish bank that has adopted FIDO methods for its customers.
FIDO leverages existing biometric methods for authentication, such as fingerprint and facial recognition, that are built-into the more recent smartphones. This means customers don’t have to go through more complex procedures to secure their transactions. Customers can also quickly check to see which of their phones and laptops have accessed their account with a list of “my secure devices,” which is a quick way to find out who has been authorized to use your account.
Banks though should be more forward-thinking and embrace FIDO, especially those banks that are moving towards having a more capable digital footprint. There are three reasons: First, account takeover fraud is rampant and increasing. Phishing lures are getting better, especially during the pandemic where customers are not necessarily paying attention to dodgy Covid-related messages that could cause a compromised account.
Second, PSD2 regulations require better authentication methods. The latest version of the Payment Services Directive of the EU has created the strong customer authentication requirement for all customer-initiated online payments and bank transfers and the EU began enforcing this requirement last year. This means when a customer wants to transfer funds, for example, they would need to make use of MFA to authenticate themselves. FIDO is one of the easiest and most secure ways to accomplish this, and the Nok Nok tools can enable this “step-up” authentication to make it seamless for the bank’s customers.
This means that authentication is not just accomplished when a customer logs into their account but as needed to safeguard their activities and protect the high risk accounts with a more secure process. The beauty of FIDO is that this protection is delivered without putting an additional burden on the user.
Finally, SMS-based authentication is a security sinkhole and can easily be compromised. The record of various stories about these compromises goes back several years. Most recently was this piece in Vice that described how one third-party utility can be used to gain access to your SMS identity without any subscriber even knowing it has been compromised. Banks really shouldn’t rely on SMS for any authentication activity.
BBVA announced last year that they began deploying Nok Nok’s software across their customer base, and since then many of their customers are using FIDO to authenticate. “Traditionally, one of the biggest challenges of authentication systems has been to balance security with user experience. Due to the FIDO standard, we are confident that both elements work together seamlessly to provide customers with the highest security standards, along with a transparent and agile user experience,” says Juan Francisco Losa, BBVA’s Global Technology and Information Security Officer.
Nok Nok has numerous banking customers using their FIDO tools, including the Iceland-based Landsbankinn and the South African-based Standard Bank. Now if only I could get my own bank on board with FIDO.