Quantum is Knocking!
Do you remember the movie Sneakers and the infamous black box labeled Setec Astronomy? That fictional device could decrypt any secret, an ability that seemed fantastic at the time. Now, quantum computers may turn that fiction into reality. These powerful machines have the potential to revolutionize our digital world, where nearly all internet communication is protected by cryptographic protocols like TLS, and our banking and payments systems rely on cryptography for card transactions and user authentication. We finally have arrived at the “too many secrets” moment hinted at in Sneakers.
Let’s dive deeper into what is driving this change, why it is urgent, and what lies ahead in this rapidly evolving space.
The Drivers
Cryptography enables us to securely encrypt information, ensuring that only authorized entities can view sensitive data, even when it is transmitted through public networks like the internet. It plays a critical role in remotely authenticating users and systems, as well as signing data to protect message integrity “at rest” and “in transit”. Essentially, cryptography is the security of the internet, since relying on dedicated communication lines without proper cryptographic protections is impractical.
Recent advances in quantum computing push the boundaries of what is possible – they are on the verge of surpassing classical computers. Certain complex problems that are challenging for classical computers can be solved more efficiently by quantum computers. The most notable example is SHOR’s algorithm, which enables quantum computers to factorize integers in polynomial time, where classical computers require exponential time. This is relevant for the RSA algorithm, which depends on the difficulty of factorization to ensure security. Note there are still (I should say: researchers believe there will be) problems which remain difficult for both classical and quantum computers, such as the “traveling salesman problem”. So in short, quantum computers are powerful, but not like the all-powerful “black box” decryption machines featured in Sneakers.
The Urgency
The NSA set 2035 as the deadline to transition to post-quantum cryptography (PQC) algorithms in national security systems. While not all systems are as sensitive as national security systems, this deadline serves as a good indicator for other industries to consider as well.
So why 2035? In the quantum computing world, performance is measured in qubits. In 2020, IBM predicted it would have a quantum computer with 1 million physical qubits by 2030. In 2023, IBM refined its projections with a more concrete plan to reach 100k physical qubits by 2033.
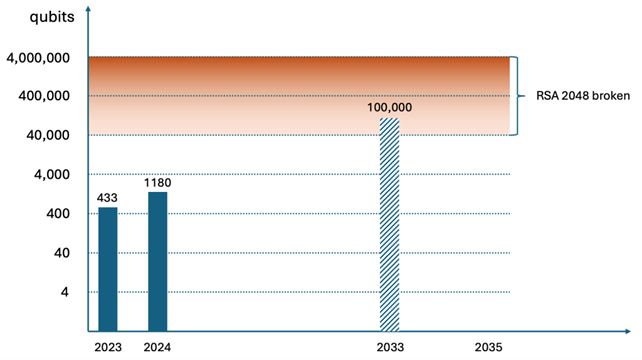
Current research suggests that 4,099 (fault-tolerant) qubits are sufficient to break RSA with 2048 bit keys – a widely used cryptographic algorithm today. This estimation assumes perfect fault-tolerant qubits. Since today’s quantum computers are very noisy, Quantum Error Correction (QEC) is required, and that adds a large qubit overhead, in the range of 10 – 100 or even up to 1000 physical qubits to implement a single fault-tolerant qubit. This means 40,000 to 4 million physical qubits are required to break RSA 2048. Based on current progress, experts predict that by 2035, quantum computers capable of breaking modern cryptographic algorithms such as RSA 2048 may exist. For context, quantum computers with 1180 physical qubits are available today, more than doubling last year’s 433 physical qubits limit.
While 2035 may seem far away, multiple factors drive a sense of urgency. In high security applications, cryptographic operations are often performed using hardware such as payment cards, hardware security modules, FIDO security keys, smartphones, and electronic ID cards. Hardware tends to have a longer lifetime than software. Especially devices like FIDO security keys and electronic ID cards that are expected to have a lifetime of 10 years, which means by 2025 there will be a demand for cryptographic hardware that is already enabled for PQC. While hardware devices, such as network communication devices or hardware security modules, might be able to add PQC support through firmware updates, others, such as FIDO security keys and electronic ID cards typically require hardware support that cannot be updated.
While it is sufficient to have PQC in place for signing and authentication use cases by 2035, encryption is a more urgent challenge. Known as “harvest now, decrypt later”, adversaries may be harvesting encrypted data hoping to decrypt it in the future using high-performance quantum computers. As a result, encryption solutions may need to be updated even sooner to mitigate this risk.
What Happens Next
NIST’s PQC project has made great progress with the publication of the first three PQC algorithms: FIPS 203, FIPS 204 and FIPS 205, and a fourth in the works.
This milestone provides the necessary clarity for protocol designers to add PQC to critical systems like TLS, FIDO, and payment networks. This in turn serves as the basis for security software products to implement PQC support.
For security engineers, especially those working on cryptographic hardware, this development is equally important. Hardware-level implementations require more lead time due to the complexity of securing firmware against side-channel attacks and other vulnerabilities. Designing, optimizing, producing, and certifying new PQC-ready chips requires more time and careful attention to ensure the security.
At that point we will see more proof-of-concept implementations and pilot deployments, eventually transitioning users to a new generation of cryptographic algorithms. In an ideal world users won’t even notice the transition and all the hard work that went into it.
As an inventor of the FIDO authentication protocol and a co-founder of the FIDO Alliance, Nok Nok continues to lead the way in supporting post-quantum cryptography. We closely monitor advances in PQC and actively help evolve the FIDO protocols to stay ahead of emerging threats. Nok Nok products are designed with built-in flexibility to support post-quantum cryptography, ensuring that our customers stay secure both now and in the future.

