Navigating the Path to Passkeys: One Approach Does Not Fit All
As businesses and government organizations embark on their journey towards implementing passkeys, careful planning and consideration of various factors are crucial to ensure a smooth transition. We think one of the most critical and valuable to the organization is “the path” – where to start, and how to stage the phases. Passkeys offer numerous benefits, including enhanced security, improved user experience, and reduced operational costs. But careful consideration of the steps that surround the actual passwordless path is critical, especially for organizations in high security and regulated markets.
What are all these steps and why are they important in migrating to Passkeys?
- Defining Goals and Priorities
Before diving into implementation, organizations must first define their specific goals and priorities for adopting passwordless technologies. Whether the aim is to bolster security measures, streamline user access, or cut down on operational expenses, clarity on objectives is essential from the outset.
- Assessing Current Security Infrastructure
With goals and priorities aligned, next up is understanding the current state of the organization’s security infrastructure. Too often organizations will miss a step as they haven’t identified potential gaps in existing solutions and assessing security posture are vital steps in preparing for the transition to passwordless authentication. This is particularly critical in industries with stringent regulatory requirements, such as finance and healthcare, where compliance and data integrity are paramount.
- Prioritizing Use Cases
Once goals are established and the security landscape is assessed, prioritizing use cases becomes the next step. Different applications and user interactions may require varying levels of security and access control. Thus, businesses must identify which use cases are most critical and prioritize them accordingly. This involves determining which use cases necessitate the highest level of security and which could benefit from a simplified user experience.
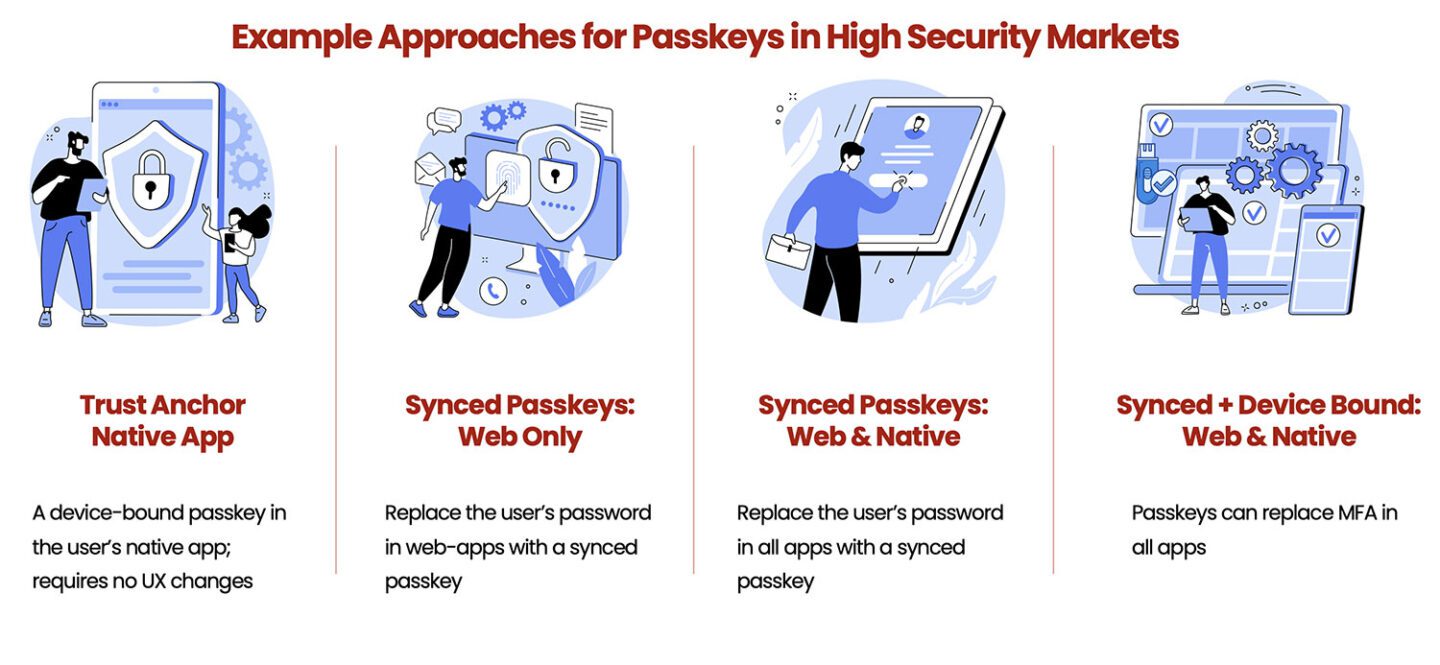
- Paths to Implementing Passwordless Solutions
With these considerations in mind, we have learned that organizations can explore various paths towards implementing passwordless solutions, each tailored to specific needs and use cases with related benefits. Where an organization starts depends on their goals and priority use cases. For example, for organizations with a mobile first strategy and high security needs, they may consider “hardening” their mobile application with a device-bound passkey first as most companies are enabling biometrics in a less secure way. This provides a “trust anchor” through the mobile app. Alternatively, businesses can opt to start by replacing passwords in applications with synced passkeys, either for web-only usage or across both web and native applications. There are pros and cons to consider and it’s important to understand the security and user experience ramifications. For high security markets, combining device bound and synced passkeys can enable organizations to address various use cases in the most convenient and secure manner.
- Planning and Rollout
While these paths may seem straightforward, transitioning to passwordless requires meticulous planning and phased rollout. Testing and refining your approach in controlled environments allows organizations to mitigate risks and make necessary adjustments based on initial feedback and performance. This approach ensures a smoother transition and enhances both security measures and user satisfaction.
For businesses seeking guidance on navigating the complexities of implementing passwordless authentication, partnering with experienced providers like Nok Nok can offer invaluable support and expertise. With over a decade of experience in deploying FIDO-based solutions for trusted brands across various industries, Nok Nok is well-equipped to assist organizations in transitioning to a passwordless future.
To learn more about accelerating your journey towards passwordless authentication, reach out to Nok Nok today.
